Avaddon virus is a dangerous ransomware that spreads via Phorphiex/Trik Botnet and excludes CIS countries from its targets
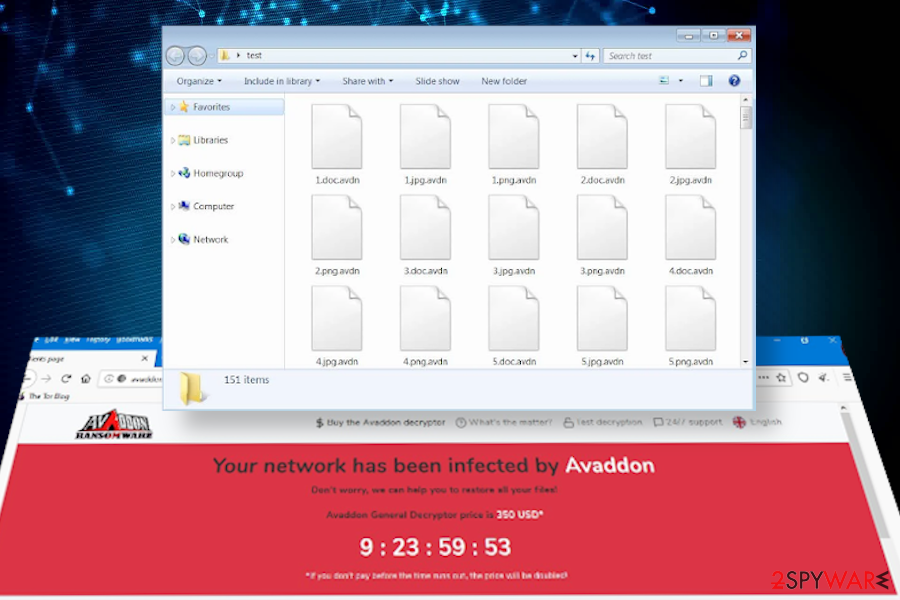

Avaddon is a cryptovirus that has been first spotted by cybersecurity researcher GrujaRS[1] in June 2020. According to experts, this ransomware can be predicted to be exceptionally active as the criminals behind it are applying all kinds of dissemination strategies, including Phorphiex/Trik Botnet, wink spam attacks, Ransomware-as-an-Affiliate (RaaS) for Russian hackers, exploit kits and more.
The executable of the Avaddon ransomware (temp27472466.exe or img164186.jpg.js) runs PowerShell and Bitsadmin commands within %Temp% to enable the ransomware. The inbuilt file encryption software scans the machine for compatible file extensions and locks the ones that it successfully recognized by happening the .avdn file extension to each of them. The virus also replaces the desktop background and creates a ransom note [id]-readme.html (instead of the ID, people see the unique identification number), which redirects to the TOR payment site, which demands victims to purchase Bitcoins and pay for the Avaddon General Decryptor 350 USD in Bitcoins.
| Name | Avaddon |
| International classification | Ransomware |
| Distribution | Phorphiex/Trik Botnet, malicious IMG123101.jpg spam attachments, unprotected RDPs, exploit kits, infected software download links, RaaS offered on Russian hacking forums, etc. |
| Related files | temp27472466.exe[2], img164186.jpg.js, sava.exe |
| File extension | The ransomware changes the extension of personal people’s files to .avdn |
| Note | As a typical file-encrypting virus, it replaces the desktop background to “All your files has been encrypted” note and generates an HTML file [id]-readme.html |
| Exclusion list | The ransomware is programmed to skip CIS countries by initiating self-destruction |
| The size of the ransomware | It’s not static. It can vary from 350 USD to 900 UAS depending on the amount of encrypted data |
| Decryptable? | .avdn files cannot be recovered for free. Experts provided the analysis of the virus and it seems that it’s using online IDs that cannot be deciphered without a unique key |
| Elimination | Automatic removal is the only option to get rid of dangerous cyber infection |
| Ransomware may trigger Windows malfunctions by compromising registries, boot files, libraries, and more. To fix suchlike damage, try running Reimage Reimage Cleaner Intego utility | |
The Avaddon ransomware virus is a newcomer to the market of crypt-extortionists. Nevertheless, experts see its potential to become a prevalent cyber threat competing with families like GandCrab, Djvu, or Jigsaw. Such presumptions are based on the activity logs and infections rate.
According to the researchers, the campaigns that criminals behind this ransomware show positive dynamics. According to the cybersecurity firm Appriver, the spams distributed via Phorphiex botnet[3] standalone reached over 300 potential victims within a few days. Even more, the ransomware can be spread by affiliate parties, Russian hackers basically, as the Avaddon ransomware virus is being offered as a Ransomware-as-an-Affiliate, paying the affiliate distributors 65% of the ransom.
However, the countries of the former Commonwealth of Independent States (CIS) are not very likely to meet this malware. According to its founders, the virus has an automatic command, which initiates Avaddon virus removal by default if the system detects the AZ, AM, BY, KZ, KG, MD, RU, TJ, UZ, UA, GE, and TM keyboard layout.
The other countries all across the world are at a high risk of getting acquainted with the .avdn file virus. Upon running the malicious sava.exe file, the virus changes the background image and creates a new directory, for example, Z folder. Besides, all personal files are locked using a sophisticated encryption algorithm (AES, RSA, ChaCha or combination) and then launches the [id]-readme.html note, which once clicked launches the TOR website and displays the following instructions:
Your network has been infected by Avaddon
All your documents, photos, databases and other important files have been encrypted and you are not able to decrypt it by yourself. But don’t worry, we can help you to restore all your files!The only way to restore your files is to buy our special software – Avaddon General Decryptor. Only we can give you this software and only we can restore your files!
You can get more information on our page, which is located in a Tor hidden network.
How to get to our page
Download Tor browser – hxxps://www.torproject.org/
Install Tor browser
Open link in Tor browser – avaddonbotrxmuyl.onion
Follow the instructions on this page
Your ID:
–DO NOT TRY TO RECOVER FILES YOURSELF!
DO NOT MODIFY ENCRYPTED FILES!
OTHERWISE, YOU MAY LOSE ALL YOUR FILES FOREVER!
The TOR website informs users about the size of the redemption (varies from $350-900) and provides a detailed guide on how to purchase Bitcoins and make the payment. In addition, people can find a support chat, a free Avaddon decryption test page, help page, and similar.
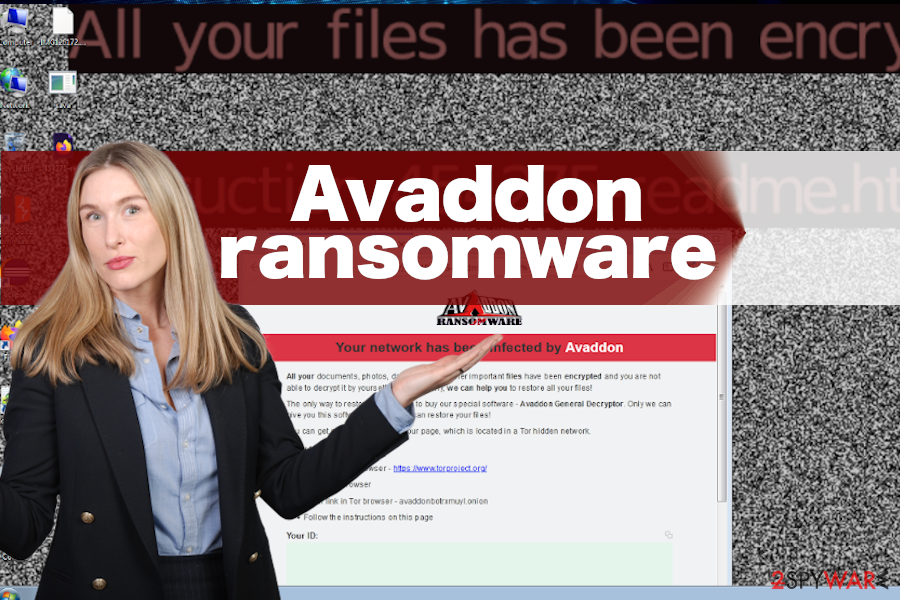
Avaddon ransomware virus changes the background, locks files, and demands to pay the ransom in Bitcoins. Otherwise, personal files will be permanently deleted

Avaddon ransomware virus changes the background, locks files, and demands to pay the ransom in Bitcoins. Otherwise, personal files will be permanently deleted
Naturally, users get a shock finding their files locked by .avdn virus files and that is understandable. Not only the fact that your access to personal files is restricted worries. However, people should also consider the fact that having a ransomware virus on the system leaves it extremely vulnerable to other cyber attacks, for example, the infiltration of Trojan or spyware.
Therefore, it’s important to remove Avaddon ransomware as soon as possible. If you found your files locked, do not hesitate and restart the system into Safe Mode to quarantine malicious processes, such as sava.exe. This way, the ransomware won’t interfere with your security tool and you will be able to launch a full system scan.
At this point, we recommend people to rely on the most robust security tool, such as SpyHunter 5Combo Cleaner, Malwarebytes, and similar. Beware that not all malicious entries run by this ransomware can be detected. Take for instance a malicious img164186.jpg.js file, which is recognized by 35 AV tools out of 65 possible. Thus, using a weak security program can end up with a failed Avaddon removal.
A multiplicity of methods are applied for spreading the ransomware all across the world
According to the researchers, this particular ransomware stands out from the crowd as its developers are spreading the ransomware in an extremely active way. The criminals themselves are using one basic dissemination strategy, known as spam.
The email messages that carry malicious attachments are being distributed by Phorphiex/Trik Botnet, which is a huge campaign capable of spreading hundreds of thousands of emails at a time (over 300,000 ar once). The details of the malicious email are the following:
- the sender – [email protected] (though it can differ)
- Subject line – “Your new photo?”
- Body text – a winking emoji
- Attachment – IMG123101.jpg
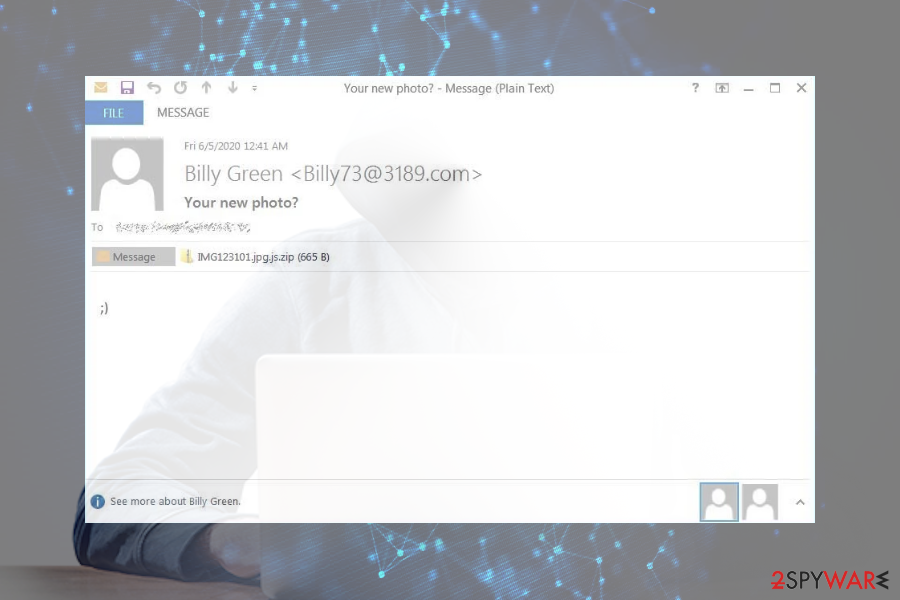
Avaddon crypto-ransomware is typically spread via malicious jpg attachments

Avaddon crypto-ransomware is typically spread via malicious jpg attachments
The jpg attachment is, in fact, a malicious JavaScript file, which once opened downloads a malicious ransomware payload. Nevertheless, this particular virus can be distributed via other means. That’s because it is offered as a RaaS, Ransomware-as-a-service, meaning that the developers of this virus are not the only ones distributing the malware. According to NoVirus.uk[4] researchers, the affiliates can render their own means of distribution to infect PCs and then collect commissions for every paid ransom fee. The other means that can be used for spreading this tool:
- Links embedded into spam emails
- Software vulnerabilities and exploit kits
- Pirated software installers
- Keygens, software cracks
- Fake Flash Player (or similar) updates
- Freeware bundles shared on shady websites
- Poorly protected Remote Desktop connections, etc.
Avaddon ransomware removal procedure
As we have already mentioned in the first part of this article, the Avaddon ransomware removal can be initiated in one way only – using a professional security program that has the latest virus database, powerful scanner, and virus removal possibilities. Our recommended programs are Malwarebytes and SpyHunter 5Combo Cleaner, but you can use any application of your preferences.
If, however, you cannot remove Avaddon virus from the system because it infringes the AV engine and keeps it disabled all the time, restart Windows OS and boot it into Safe Mode with Networking. This way, all malicious processes will be disabled and you will be able to start the security scan.
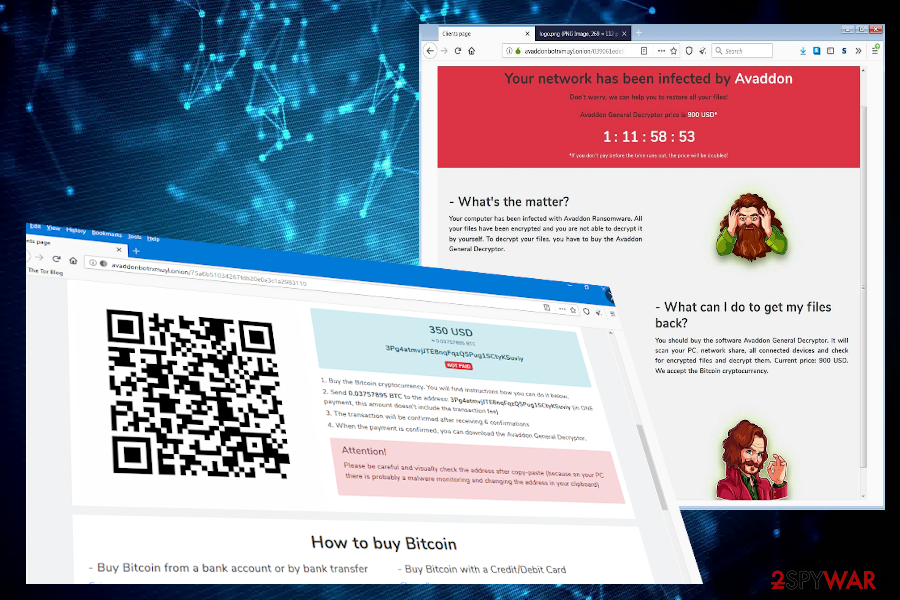
Avaddon ransom note redirects to TOR payment site, which explains what happened and explains how to purchase Bitcoins

Avaddon ransom note redirects to TOR payment site, which explains what happened and explains how to purchase Bitcoins
Once the ransomware is removed, you can start thinking about the recovery of the .avdn files. As pointed out by cybersecurity experts, there’s no free decryptor for this virus. Therefore, you should select if you are going to pay the ransom (not recommended), use backups, or apply alternative data recovery methods listed below.
The government has many issues in regards to tracking users’ data and spying on citizens, so you should take this into consideration and learn more about shady information gathering practices. Avoid any unwanted government tracking or spying by going totally anonymous on the internet.
You can choose a different location when you go online and access any material you want without particular content restrictions. You can easily enjoy internet connection without any risks of being hacked by using Private Internet Access VPN.
Control the information that can be accessed by government any other unwanted party and surf online without being spied on. Even if you are not involved in illegal activities or trust your selection of services, platforms, be suspicious for your own security and take precautionary measures by using the VPN service.
Computer users can suffer various losses due to cyber infections or their own faulty doings. Software issues created by malware or direct data loss due to encryption can lead to problems with your device or permanent damage. When you have proper up-to-date backups, you can easily recover after such an incident and get back to work.
It is crucial to create updates to your backups after any changes on the device, so you can get back to the point you were working on when malware changes anything or issues with the device causes data or performance corruption. Rely on such behavior and make file backup your daily or weekly habit.
When you have the previous version of every important document or project you can avoid frustration and breakdowns. It comes in handy when malware occurs out of nowhere. Use Data Recovery Pro for the system restoring purpose.
This entry was posted on 2020-06-12 at 07:36 and is filed under Ransomware, Viruses.

