Mespinoza ransomware – cryptomalware that encrypts data of local governments
Mespinoza ransomware is a data locker that mainly targets high-profile organisations and businesses worldwide

Mespinoza ransomware is a data locker that mainly targets high-profile organisations and businesses worldwide
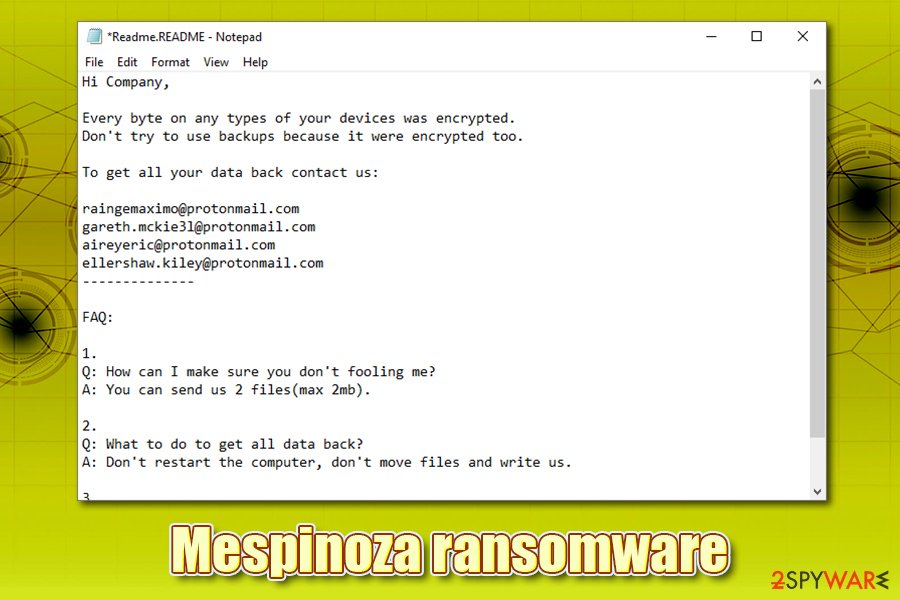
Mespinoza ransomware, otherwise known as Pysa ransomware, is a data locking virus that was first seen attacking organizations and local authorities in October 2019. Just as any other malware of this type, its main goal is to make money by locking all personal files on local and networked drives, and then ask for a ransom for decryption software. Mespinoza virus performs the encryption with the help of AES cipher and appends all files with .locked marker, preventing owners from accessing them. In later versions, the malware also uses .pysa and .newversion markers.
After file encryption, Mespinoza ransomware delivers Readme.README file, which is placed on users’ desktop, as well as various other locations of Windows. In the brief note, the attackers explain what happened to victims’ machines and that they need to send an email to a particular email address (multiple different ones are used, including raingemaximo@protonmail.com, mckie31@protonmail.com, aireyeric@protonmail.com, ellershaw.kiley@protonmail.com, and others) to contact the Mespinoza virus authors.
| Name | Mespinoza ransomware |
| Type | File locking virus, cryptomalware |
| Also known as | Pysa ransomware |
| Malware family | Vurten malware family |
| Encryption method | The malware uses AES encryption algorithm to lock pictures, documents, databases, videos, and other personal or company files |
| Extension | Extension depends on the version of the virus – these are: .locked, .pysa, and .newversion |
| Ransom note | Readme.README is dropped into various folders on the system, as well as the desktop |
| Contact | mespinoza980@protonmail.com, alanson_street8@protonmail.com, lambchristoffer@protonmail.com, aireyeric@protonmail.com, ellershaw.kiley@protonmail.com, raingemaximo@protonmail.com, gareth.mckie31@protonmail.com |
| Termination | To get rid of the infection, users should scan their computers with anti-malware software. If the virus terminates the security tool, accessing Safe Mode with Networking would bypass this functionality |
| Data recovery |
There is no secure and 100% effective way of recovering data without backups. The other options as follow:
|
| System fix | In case termination of malware did not fix Windows and it started crashing, lagging, or suffer from stability issues, users should employ Reimage Reimage Cleaner Intego or a similar tool to fix virus damage |
Mespinoza ransomware has its roots in Vurten ransomware, which was first released in April 2018 by unknown cybercriminals who demanded as much as $10,000 for the decryption software. Currently, it is unknown what the demands of this strain are, although it is likely to be high as well. The attackers ask to pay in Bitcoin, although other cryptocurrencies are sometimes accepted as well. In mid-March 2020, Mespinoza ransomware was spotted attacking local governess in France.[1]
While there is no working Mespinoza ransomware decryptor currently available, paying cybercriminals is not advisable, as they might simply scam victims. The best way to recover data is by using backups, although there are also third-party tools that users could rely on. Nonetheless, before proceeding with the data recovery process, Mespinoza ransomware removal should be performed by using anti-malware software.
Mespinoza virus uses plenty of tricks to avoid detection
Security researchers from CERT-FR who recently dealt with Mespinoza ransomware attack on French governments claimed that it is yet unclear how the threat is propagated,[2] although some indicators pointed that brute-forcing and Remote Desktop connection is most likely used. Nevertheless, because malware mainly focuses on companies instead of regular users, another common tactic – spear phishing[3] – might also be employed by malicious actors.
Mespinoza virus is the latest ransomware family that joined the “big game hunting” – a tactic used to attack high-profile organizations in the hopes of extorting larger sums of ransoms. Other known strains that infect companies in targeted attacks include:
Once Mespinoza ransomware breaks into a machine, it also infects all the attached networks. Essentially, if backups are stored on these networks, they will get encrypted as well, rendering them useless, so it is vital to ensure that backups are held on a separate network or even offline. Before encrypting data, the Mespinoza file virus will deploy the PowerShell Empire penetration testing program that allows the attackers to stop anti-malware protection tools.
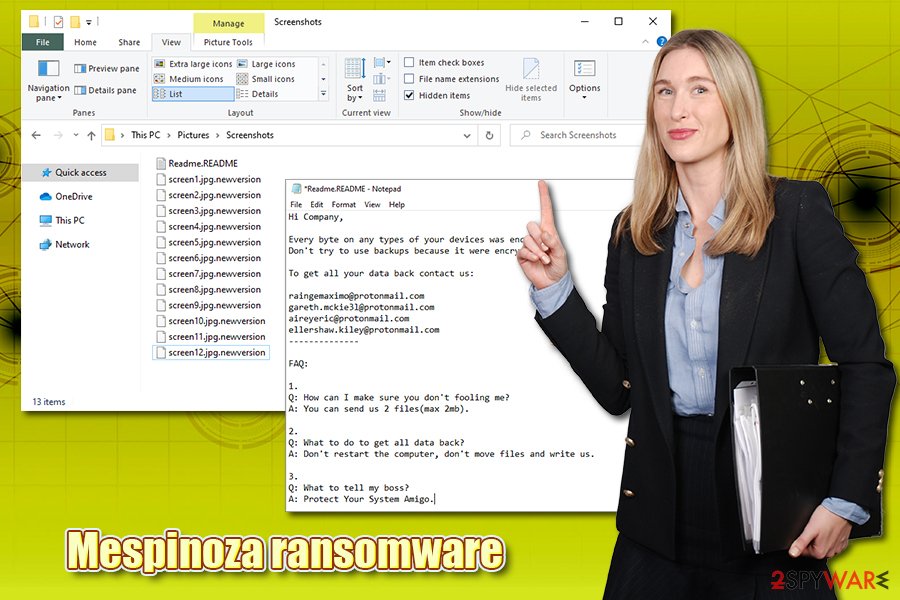
Mespinoza ransomware is a file locking virus that uses AES encryption algorithm to lock all data on local and networked drives

Mespinoza ransomware is a file locking virus that uses AES encryption algorithm to lock all data on local and networked drives
Following typical modifications to the Windows registry, deletion of Shadow Volume Copies and other changes, and creation of malicious files as well as processes, Mespinoza ransomware will also inject additional modules to Google Chrome web browser, which allows all the sensitive information to be transferred to the attackers.[4] This is another reason to remove Mespinoza ransomware from the system as soon as possible.
After the necessary changes are made and networks infected, the malware begins a scan that targets the most commonly used files in an enterprise and home environment to cause maximum damage to victims. Since its release, Mespinoza virus used .locked, .pysa, and, most recently, .newversion file extension. Following the encryption, the malware drops a note which reads:
Hi Company,
Every byte on any types of your devices was encrypted.
Don’t try to use backups because it were encrypted too.To get all your data back contact us:
raingemaximo@protonmail.com
gareth.mckie3l@protonmail.com
aireyeric@protonmail.com
ellershaw.kiley@protonmail.com
————–FAQ:
1.
Q: How can I make sure you don’t fooling me?
A: You can send us 2 files(max 2mb).2.
Q: What to do to get all data back?
A: Don’t restart the computer, don’t move files and write us.3.
Q: What to tell my boss?
A: Protect Your System Amigo.
Besides encrypting data, Mespinoza ransomware also extracts certain information from the infected network, which includes a database of the company’s account and password information, most likely to elevate permissions even further.
However, other malware strains that encrypted data on companies’ computers started a new trend – they threaten to expose sensitive data online if the ransom is not paid, compromising operations of the organization. In some cases, such an unfortunate turn of events can lead to the company’s closure and data exposure of innocent people.
To eliminate Mespinoza ransomware, a network-wide scan should be initiated and IT staff employed for the job. If the company had backups, ransom payment should never be paid (unless the attackers threaten to expose sensitive data, although it unclear whether the Mespinoza virus gathers such information). To fix the infection caused damage to the operating system, a repair software like Reimage Reimage Cleaner Intego can be used.
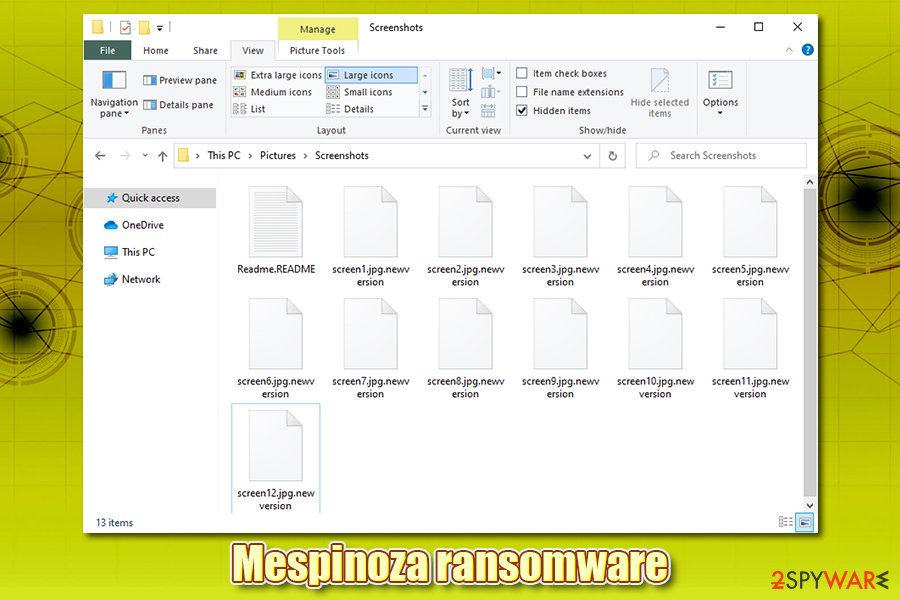
Mespinoza ransomware is currently not decryptable, and backups is the only secure method to recover files without paying the attackers

Mespinoza ransomware is currently not decryptable, and backups is the only secure method to recover files without paying the attackers
Ransomware prevention tips
While it is currently not precisely known how Pysa ransomware is distributed, there are several precautionary measures that companies, businesses, local governments, and regular users. Ransomware strains like Djvu rely on random infection vectors such as software cracks – those who access compromised sites and download the malicious executable get infected.
Nevertheless, when it comes to companies, such a malware distribution method would not be appropriate, as it would not reach the desired targets. Due to this, the attackers employ methods that would work well for targeted attacks, such as weakly protected RDP connections, leaked credential databases, brute force attacks, and similar.
To prevent ransomware intrusions, you should be practicing the following security measures:
- Equip every computer on the network with a comprehensive anti-malware protection;
- Update each of the machines and the installed software as soon as patches are deployed;
- Do not open spam email attachments unless you are sure that they are legitimate;
- Don’t allow a macro function to run on documents, PDF and other files that might be delivered via the email;
- Only allow relevant staff to use Remote Desktop connection and protect with a VPN;
- Never use a default TCP/UDP open ports;
- Employ alphanumeric passwords when connecting yo RDP or accessing the machine/network;
- Educate staff about cybersecurity and safe computer practices.
Most importantly, you should ensure that backups are constantly updated and not connected to the main network.
Mespinoza ransomware removal process
It is important to note that you should not remove Mespinoza ransomware immediately, although modules that can gather sensitive information and disable security software might point otherwise. However, if you start the virus termination before you backup encrypted files, they might be corrupted permanently. If you have a working copy of your most important files, however, you can proceed with Mespinoza ransomware removal without delays.
As previously mentioned, the termination process of the Mespinoza virus from an entire network should be performed with the help of IT professionals, as malware is known to disable the anti-virus protection upon infiltration – this can cause troubles when trying to eliminate the infection. Nevertheless, the process can be performed much easier in Safe Mode with Networking – you can find instructions on how to access it below.
If you had no backups, paying the attackers for the data recovery tool might be your only option if you desperately need your files back. However, you should first try to use third-party recovery tools or other methods listed below.
This entry was posted on 2020-03-24 at 07:31 and is filed under Ransomware, Viruses.

