ATKL ransomware is the dangerous malware because it contaminates systems and causes serious problems besides file encryption

ATKL ransomware – cryptovirus that drops random files on the machine, interferes with processes, applications, and programs to avoid quick virus termination or file recovery. It locks commonly used files and demands payment from victims promising to send the decryption tool after that. However, this is a version of Matrix ransomware that is known for more than a few years, and none of the variants can be decrypted. As a typical ransomware-type virus, this threat starts with file encryption and money demand, so when the time for payment ends, the system is affected in various ways. Cybercriminals change the original code of the image, document, audio, or video file and then marks the affected data using .ATKL extension with the contact email address. For example, if your Image.jpg file gets locked it becomes Image.jpg.[[email protected]].[random_string].ATKL. The email address may change because criminals provide at least three of them ([email protected], [email protected], and [email protected]).
ATKL ransomware virus developers encourage people to contact them via these emails and do that as soon as possible, so the payment can become a decryption possibility, as they claim. We don’t recommend trusting these people because malicious actors have their own goals of getting money directly from you and stealing possibly valuable data from machines and other accounts online. All these instructions, claims, and promises get listed in the ransom message that appears as a !ATKL_README!.rtf file on the screen. Do not fall for the test decryption possibility and keep away from these people at all. Contacting them alone can bring more issues, additional malware. The ransomware infection on its own can damage many parts of the computer, so clean the device as soon as possible.
| Name | ATKL ransomware |
|---|---|
| Family | Matrix |
| File marker | .[[email protected]].[random_string].ATKL appears on the encrypted data and can differ from victim to victim because the email may get changed. The random string included in this pattern can be related to victims’ ID listed on the ransom message file |
| Ransom note | !ATKL_README!.rtf – the message encouraging people to pay the ransom for file decryption. This is a lengthy note containing instructions, contact information, offer for test decryption and your personal ID needed for the decryption |
| Contact emails | [email protected], [email protected], and [email protected] |
| Additional feature | The malware drops random files on the machine that can be found on the desktop and in other folders. There is no particular usage for them, and types of data differ |
| Danger | This ransomware deletes Shadow Volume Copies to ensure that there are fewer options for data recovery and manages to alter or add new registry keys that interfere with system functions and applications running on the device. This s threat based on blackmailing, so anything can lead to money or data loss or permanent damage on the infected computer |
| Distribution | This is the widespread threat that manages to distribute payload using exploit kits like RIG,[1] hacked sites, malicious pages, and infected files attached to emails. |
| Elimination | To remove ATKL ransomware completely, get a tool that can possibly detect[2] this malware and other associated applications or files and delete them completely |
| Repair | As for data affected by the virus. System files get damaged and corrupted, so various processes cannot run and help you with recovery and cleaning, so run Reimage Reimage Cleaner Intego and fix that damage, affected data and repair functions of the OS |
ATKL ransomware makes files no longer accessible for users, so they cannot even know which data is valuable. It creates frustration and even panic because file restoring is almost impossible if you don’t have any data backups on external devices or cloud services. Especially, when the ransom gets demanded for the alleged decryption options. The tool that criminals promise to have may not even exist, and the second your money gets transferred, they disappear without any opportunity to contact virus creators again. This is one of the main reasons to not communicate with threat actors.
Also, remember that ATKL ransomware is a version of the dangerous threat, so virus developers know how to avoid detections, encode files permanently and evade security, AV tools. This cryptovirus uses powerful encryption algorithms and modifies the structure of data, so there are no other options, but to pay the ransom. No matter how small it is – DO NOT PAY.
There are too few chances that files affected by the threat will get recovered fully. You better remove ATKL ransomware and clean the machine, then go for the cleaning processes and system repair, data recovery. Before restoring anything, make sure that the threat is no longer active, and there is nothing possibly associated with the virus or additional malware. Your files may get permanently damaged if the virus runs another round of encryption.
ATKL ransomware starts with encryption, but this is not the only process it can run on the infected machine, so once you get this ransom demanding message, make sure to react and clean the system with anti-malware tools.
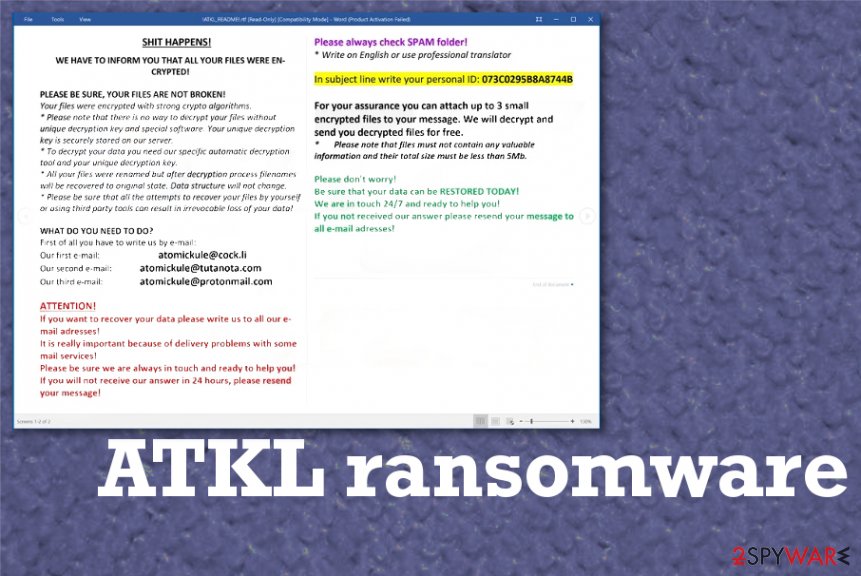
SH*T HАPPENS!
WE HАVE TО INFОRM YОU THАT АLL YОUR FILES WERE ENCRYPTED!PLEАSE BE SURE, YОUR FILES АRE NОT BRОKEN!
Yоur filеs wеrе еnсrуptеd with strоng сrуptо аlgоrithms.
* Plеаsе nоtе thаt thеrе is nо wау tо dесrуpt уоur filеs withоut uniquе dесrуptiоn kеу аnd spесiаl sоftwаrе. Yоur uniquе dесrуptiоn kеу is sесurеlу stоrеd оn оur sеrvеr.
* Tо dесrуpt уоur dаtа уоu nееd оur spесifiс аutоmаtiс dесrуptiоn tооl аnd уоur uniquе dесrуptiоn kеу.
* Аll уоur filеs wеrе rеnаmеd but аftеr dесrуptiоn prосеss filеnаmеs will bе rесоvеrеd tо оriginаl stаtе. Dаtа struсturе will nоt сhаngе.
* Plеаsе bе surе thаt аll thе аttеmpts tо rесоvеr уоur filеs bу уоursеlf оr using third pаrtу tооls саn rеsult in irrеvосаblе lоss оf уоur dаtа!WHАT DО YОU NEED TО DО?
First оf аll уоu hаvе tо writе us bу е-mаil:
Оur first е-mаil: [email protected]
Оur sесоnd е-mаil: [email protected]
Оur third е-mаil: [email protected]АTTENTIОN!
If уоu wаnt tо rесоvеr уоur dаtа plеаsе writе us tо аll оur е-mаil аdrеssеs!
It is rеаllу impоrtаnt bесаusе оf dеlivеrу prоblеms with sоmе mаil sеrviсеs!
Plеаsе bе surе wе аrе аlwауs in tоuсh аnd rеаdу tо hеlp уоu!
If уоu will nоt rесеivе оur аnswеr in 24 hоurs, plеаsе rеsеnd уоur mеssаgе!
Plеаsе аlwауs сhесk SPАM fоldеr!
* Writе оn English оr usе prоfеssiоnаl trаnslаtоrIn subjесt linе writе уоur pеrsоnаl ID: –
Fоr уоur аssurаnсе уоu саn аttасh up tо 3 smаll еnсrуptеd filеs tо уоur mеssаgе. Wе will dесrуpt аnd sеnd уоu dесrуptеd filеs fоr frее.
* Plеаsе nоtе thаt filеs must nоt соntаin аnу vаluаblе infоrmаtiоn аnd thеir tоtаl sizе must bе lеss thаn 5Mb.Plеаsе dоn’t wоrrу!
Bе surе thаt уоur dаtа саn bе RESTОRED TОDАY!
Wе аrе in tоuсh 24/7 аnd rеаdу tо hеlp уоu!
If уоu nоt rесеivеd оur аnswеr plеаsе rеsеnd уоur mеssаgе tо аll е-mаil аdrеssеs!

ATKL ransomware – cryptovirus that relies on cryptography and malicious files that get added in various places to control the applications and performance.

ATKL ransomware – cryptovirus that relies on cryptography and malicious files that get added in various places to control the applications and performance.
Even though ATKL ransomware developers claim to offer you the decryption tool and even encourage to test decrypt 3 files, you shouldn’t even bother and think about that. Ignore the message and remove the virus. You may store some of the encrypted files and virus-related data on a separate external device if you think that a decryption tool can be developed later on. However, the time is important with these threats because anything can get installed in the background without your knowledge and permission.
ATKL ransomware removal process gets difficult due to affected programs, security functions, and questionable files added in various places of the machine. It is unknown why and for what purpose those files and programs get added on the desktop, but malware can freely affect system processes launching applications and disabling running functions. You need to repair those features after virus termination too, so using Reimage Reimage Cleaner Intego can be crucial for the state of security.
Such PC repair utilities or system optimizers can find and fix ATKL ransomware virus damage, affected or even corrupted files, functions. Make sure to take care of these issues before you go further with any data recovery options to avoid permanent damage or loss.
Also, ATKL ransomware belongs to a family of threats that distributes variants using sophisticated and powerful methods like exploit kits, hacked or malicious sites. Various vulnerable programs might get used to installing ransomware and other viruses like worms or information-stealing trojans.
Proper termination procedures are needed to tackle all ATKL ransomware virus-associated intruders and malware, so rely on the anti-malware tools that can possibly detect such powerful viruses and remove them from the devices. For additional tips, we have prepared a few solutions below. Also, decryption options for those who have not backed up their data in advance. 
ATKL ransomware is the virus that marks data using contact email and identificational characters after encryption.

ATKL ransomware is the virus that marks data using contact email and identificational characters after encryption.
Sophisticated methods of spreading crypto-extortion based malware
The infection like this can spread various ways, depending on the particular campaign and version of the threat, malicious actors. Spam email campaigns with infected email attachments that trigger macros[3] are more common for the ransomware viruses. Also, exploit kits, vulnerabilities, and malicious programs designed for dropping the payload are used more often than other techniques.
It is known that the particular ransomware family creates shortcuts on the infected machines to spread on other computers. The copy of the ransomware executable file gets hidden in the folder and modified into a shortcut. Once clicked it launches the program and executes ransomware that either encrypts files newly added on the same machine or infects another computer via network shares or removable drives.
It is known that these methods can be updated and changed quickly, so remain cautious and clean the email box more often, avoid opening any email notifications or files attached to the email and clean the machine from viruses and vulnerable applications more often using the proper system or security tools.
ATKL ransomware infection termination guide
Since this ATKL ransomware virus is one of many versions in the known and dangerous virus family, you should take the additional issues into consideration. Executable files, applications, and programs that get disabled all are results of the infection.
Ransomware ensures that you, as a victim, have fewer options for virus termination and even file recovery so malware can run longer on the machine. Make sure to remove ATKL ransomware as soon as you can and rely on proper anti-malware tools, don’t look for an easy way out.
We recommend going for automatic ATKL ransomware removal using SpyHunter 5Combo Cleaner or Malwarebytes because these security programs can find virus-related data and terminate those malicious processes for you. Also, tools like Reimage Reimage Cleaner Intego can ensure that nothing is missed and all OS functions are back to normal and running. Always double-check before adding anything new on the machine, especially before data recovery.
Remove ATKL using Safe Mode with Networking
Reboot the system in Safe Mode with Networking and run your AV tool for proper ATKL ransomware virus termination
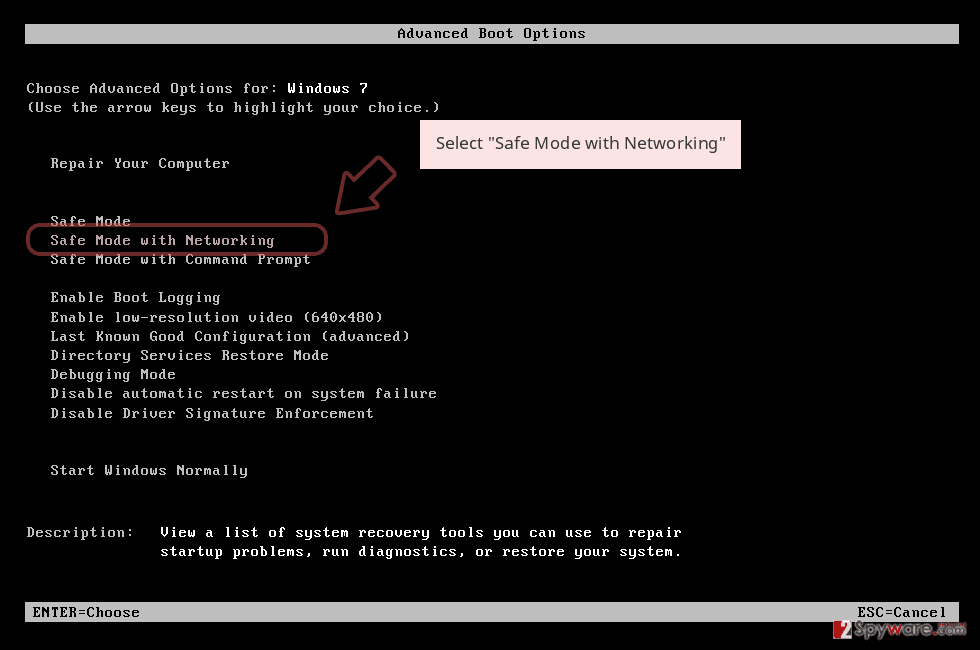
- Windows 7 / Vista / XP
- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list
Windows 10 / Windows 8
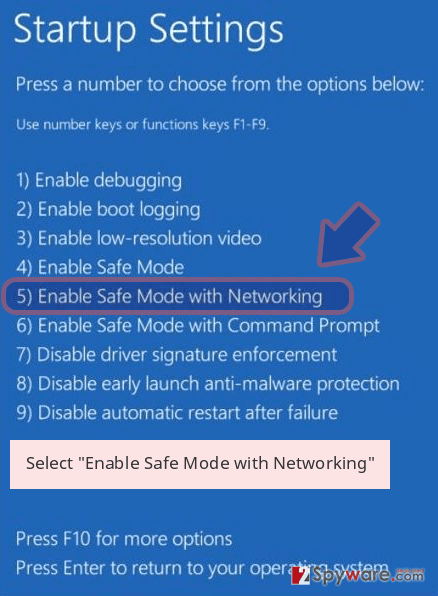
- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
- Once your computer becomes active, select Enable Safe Mode with Networking in Startup Settings window.
-
Log in to your infected account and start the browser. Download Reimage Reimage Cleaner Intego or other legitimate anti-spyware program. Update it before a full system scan and remove malicious files that belong to your ransomware and complete ATKL removal.
If your ransomware is blocking Safe Mode with Networking, try further method.
Remove ATKL using System Restore
System Restore can help you with this virus because it allows recovering the machine in a previous state
Bonus: Recover your data
Guide which is presented above is supposed to help you remove ATKL from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.
If your files are encrypted by ATKL, you can use several methods to restore them:
Data Recovery Pro can restore files after encryption for you
When ATKL ransomware virus damaged your files, or you accidentally deleted them yourself, you can rely on Data Recovery Pro and restore files
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by ATKL ransomware;
- Restore them.
Windows Previous Versions feature possibly recovers individual files for you
System restore should be enabled before, so Windows Previous Versions can properly recover your data
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
ShadowExplorer – a method for file restoring
When threats like ATKL ransomware virus are not affecting Shadow Volume Copies, you can use the system feature for data recovery
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Decryption for files affected by the ATKL ransomware is not possible
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from ATKL and other ransomwares, use a reputable anti-spyware, such as Reimage Reimage Cleaner Intego, SpyHunter 5Combo Cleaner or Malwarebytes
This entry was posted on 2020-03-18 at 04:53 and is filed under Ransomware, Viruses.

